In today’s technology-driven world, effective IT governance processes and policies play a crucial role in ensuring the optimal management, utilization, and security of information technology within organizations. With the increasing complexity and interconnectedness of IT systems, businesses must establish robust governance frameworks to align IT activities with business goals, mitigate risks, and ensure compliance. In this blog post, we will delve into the fundamentals of IT governance, explore key processes and policies, and highlight their significance in promoting organizational success.
What is IT Governance?
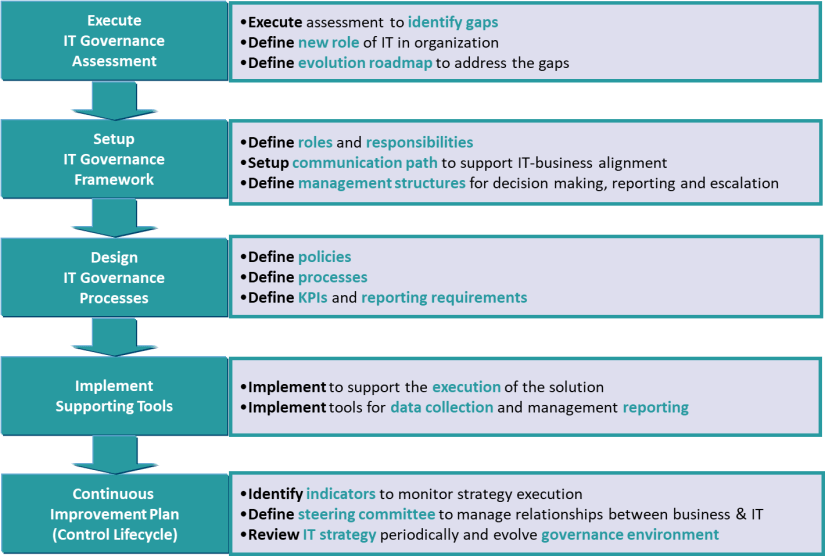
IT governance encompasses the frameworks, processes, and policies that enable organizations to make informed decisions regarding IT investments, resource allocation, risk management, and performance measurement. It provides a structured approach for aligning IT strategies with business objectives, optimizing IT resources, and ensuring the delivery of value to stakeholders.
Key IT Governance Processes
- Strategic Alignment: Strategic alignment ensures that IT initiatives are closely aligned with the organization’s overall business strategy. It involves establishing mechanisms to identify business requirements, defining IT goals, and developing plans that align IT projects and investments with strategic objectives.
- IT Risk Management: IT risk management involves identifying, assessing, and mitigating risks associated with IT systems and infrastructure. This process helps organizations safeguard sensitive information, protect against cybersecurity threats, and ensure business continuity by implementing appropriate controls, policies, and procedures.
- Resource Management: Effective resource management focuses on optimizing the allocation and utilization of IT resources such as hardware, software, and personnel. This process ensures that resources are allocated efficiently, projects are adequately staffed, and IT assets are managed and maintained to maximize their value.
- Performance Measurement: Performance measurement involves defining key performance indicators (KPIs) to assess the effectiveness and efficiency of IT operations. Regular monitoring and measurement of KPIs provide insights into IT performance, enabling organizations to identify areas for improvement, optimize processes, and drive innovation.
Key IT Governance Policies
- IT Security Policy: An IT security policy outlines guidelines and practices for safeguarding sensitive information, preventing unauthorized access, and maintaining data integrity. It covers areas such as data encryption, access controls, incident response, and employee awareness training to ensure a secure IT environment.
- Data Privacy Policy: A data privacy policy defines how an organization collects, handles, and protects personal and sensitive information in compliance with applicable data protection regulations. It addresses issues such as consent, data retention, data transfer, and individual rights, fostering trust and transparency with customers and stakeholders.
- IT Service Management Policy: An IT service management policy establishes standards and procedures for delivering IT services to internal users and external customers. It covers areas such as service level agreements (SLAs), incident management, problem management, and change management, ensuring consistent and reliable IT service delivery.
- IT Procurement Policy: An IT procurement policy sets guidelines for acquiring IT hardware, software, and services. It ensures that procurement processes are transparent, competitive, and aligned with organizational needs, while also considering factors such as vendor evaluation, contract negotiation, and compliance with licensing requirements.
Benefits of Effective IT Governance
Implementing robust IT governance processes and policies offers several benefits to organizations, including:
- Enhanced Decision Making: IT governance provides a framework for informed decision making, enabling organizations to prioritize IT investments, allocate resources effectively, and align IT initiatives with business goals.
- Risk Mitigation: By implementing risk management practices and security policies, IT governance helps organizations identify and mitigate IT-related risks, safeguard sensitive information, and protect against cyber threats.
- Increased Operational Efficiency: Well-defined processes and policies streamline IT operations, optimize resource allocation, and improve overall efficiency, resulting in cost savings and enhanced productivity.
- Regulatory Compliance: IT governance ensures adherence to industry-specific regulations and data protection laws, mitigating legal and financial
An effective IT Governance organization structure
An effective IT governance organization structure is crucial for ensuring the successful implementation and management of IT governance practices within an organization. While specific structures may vary depending on the organization’s size, industry, and complexity, here is a typical framework for an IT governance organization structure:
- IT Governance Steering Committee: The IT Governance Steering Committee serves as the highest-level governing body responsible for overseeing and guiding IT governance initiatives. It is typically composed of senior executives, such as the Chief Information Officer (CIO), Chief Technology Officer (CTO), Chief Financial Officer (CFO), and other relevant stakeholders. The committee sets the strategic direction, establishes policies, and ensures that IT governance aligns with business objectives.
- IT Governance Office/Group: The IT Governance Office or Group operates as the central coordinating body for IT governance activities. It facilitates the development, implementation, and ongoing monitoring of IT governance processes and policies. The office/group is responsible for providing guidance, ensuring compliance, and promoting awareness and understanding of IT governance across the organization. It may also assist in measuring and reporting IT governance performance.
- IT Governance Subcommittees: These subcommittees focus on specific areas of IT governance and report to the IT Governance Steering Committee. Examples of subcommittees include:a. IT Risk Management Subcommittee: Responsible for identifying, assessing, and managing IT risks throughout the organization. It establishes risk management frameworks, defines risk appetite, and ensures appropriate controls are in place.b. IT Security Subcommittee: Deals with information security, cybersecurity, and data protection. It establishes security policies, oversees security audits, and ensures compliance with relevant regulations and standards.c. IT Strategy and Alignment Subcommittee: Focuses on aligning IT strategies with business objectives. It oversees IT planning processes, investment prioritization, and the evaluation of technology trends and innovation.d. IT Performance Measurement Subcommittee: Responsible for defining and monitoring key performance indicators (KPIs) related to IT governance. It ensures the collection of relevant data, conducts performance assessments, and provides insights for continuous improvement.
- IT Governance Champions/Representatives: These individuals or teams serve as ambassadors for IT governance within different departments or business units. They facilitate the implementation of governance practices, act as a point of contact for governance-related issues, and promote awareness and compliance at the operational level.
- IT Governance Working Groups: These groups consist of subject matter experts and stakeholders from various areas of the organization. They collaborate on specific IT governance initiatives, projects, or process improvements. Working groups contribute to the development and implementation of governance policies, frameworks, and best practices.
- IT Governance Liaison: A designated liaison between the IT governance organization and other key business functions, such as legal, compliance, and audit. This role ensures effective communication, coordination, and collaboration between IT governance and these functions to address regulatory requirements and maintain alignment.
It is important to note that the structure described above can be tailored to fit the specific needs and characteristics of each organization. The size and complexity of the organization, industry regulations, and corporate culture all influence the structure and composition of the IT governance organization.